According to a survey, 77% of companies use penetration testing to check for vulnerabilities in their systems. In the face of increasing vulnerabilities, this is a sound approach to achieving a stronger cybersecurity posture. But when it comes to black box vs white box penetration testing, which one should you choose?
In this blog, we will go over both pen testing methods and compare their pros and cons to help you choose the right penetration testing technique.
Why Is Penetration Testing Important?
Penetration testing helps you get a realistic view of where your cybersecurity defenses stand. If there were to be a malicious attack on your network or systems, pen testing tells you how well would you be able to ward off the threat.
The ever-evolving threat landscape is wrought with vulnerabilities. The total number of vulnerabilities reported in 2022 was over 25,000. The cost of a data breach on account of these vulnerabilities can cost an organization millions of dollars. Penetration testing is important since it can discover vulnerabilities early on and help you take remedial action in time to prevent major data breaches.
Read more: Why, When, and How Often is Pen Testing Needed?
What Is Penetration Testing?
Forbes notes that a penetration test (pen-test) is often confused with a vulnerability scan, a compliance audit, or a security assessment. Penetration goes beyond those system checks and does the following:
Takes Vulnerability Scan Information to the Next Level.
If you discover vulnerabilities during a pen-test, you can exploit those vulnerabilities to prove, or disprove, real world attack potential.
Focuses on the Individual or Team of Testers.
It is important to try to understand possible motive over sophisticated modalities in this type of testing.
Seeks Information About Real-World Effectiveness of Your Security System.
Again, motive is key with penetration testing. You are trying to determine whether your system, no matter how advanced your security, can stand up to a resolute, stealthy, and ruthless hacker.
Considers Multiple Attack Vectors Against the Same Target.
Limiting your scope of threats—such as only focusing on your internet browser vector—limits your understanding of your system and your readiness to protect it.
There Is Even More to Penetration Testing: Black Box vs. White Box
To further specify the type of testing you need to do, and the ultimate understanding that your IT team needs to grasp about your system, you need to choose between performing a black box or a white box pen-test.
Black Box Penetration Testing
Basically, this type of testing gives no advanced notice to your tester, or testers, that you will be performing a pen-test. Fans of this type of testing believe that testing should be carried out without privileged knowledge of the target, or targets, per ScienceDirect.
This “blind testing” tack forces the tester to spontaneously find an open route access into the network. Ideally, the tester will not find any breaches, but if you do, this type of testing gives you the perfect opportunity to make corrections before an actual hacker finds that same route, just as haphazardly as your tester found it.
Additional features and benefits of black box testing include the following:
- Applicable to Nearly Every Level of Software Testing.
- Tester Knows What to Do but Not How to Do It.
- Promotes the Achievement of More Accurate Results.
When is Black Box Testing Used?
Black box testing can be used in the scenarios described below.
- You need to perform an external assessment of the system.
When you want to test the security posture of a system (or network) from an external perspective, black box testing can come in handy. It can help to simulate the different techniques hackers might use to breach your system.
- You are performing the test on large or complex systems.
When the system is large or complex, examining the code might not be feasible. In such cases, black box pen testing can be a good choice to evaluate the system’s defenses.
- You need to test system performance under real-world conditions.
Black box pen testing is the closest you can get to an actual breach attempt by a potential hacker. It can show you exactly how your system will respond to an actual attack and whether it is capable of warding off the attack.
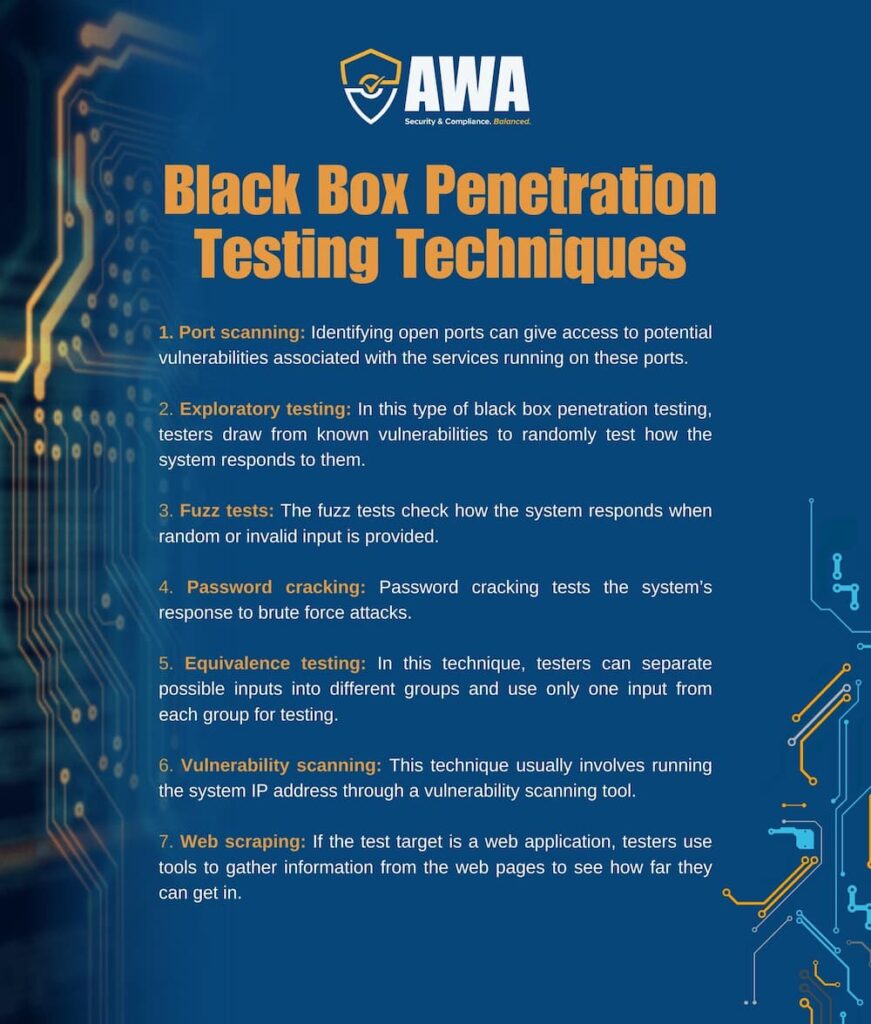
Common Black Box Penetration Testing Techniques
There are several black box penetration testing techniques. Some of the common testing techniques are the following.
- Port scanning: Port scanning looks for open ports by scanning all of the system’s ports. Identifying open ports can give access to potential vulnerabilities associated with the services running on these ports.
- Exploratory testing: In this type of black box penetration testing, testers draw from known vulnerabilities to randomly test how the system responds to them.
- Fuzz tests: The fuzz tests check how the system responds when random or invalid input is provided. These tests help to determine whether the system would crash or demonstrate unexpected behavior when invalid input is deliberately fed into the system.
- Password cracking: Password cracking tests the system’s response to brute force attacks. It can also uncover vulnerabilities where system passwords can be bypassed.
- Equivalence testing: In this technique, testers can separate possible inputs into different groups and use only one input from each group for testing. For example, for input groups based on age, where each group would have a distinct outcome, testing just one value from each age group range would be enough.
- Vulnerability scanning: This technique usually involves running the system IP address through a vulnerability scanning tool. The tool checks the system against pre-defined vulnerabilities.
- Web scraping: If the test target is a web application, testers use tools to gather information from the web pages to see how far they can get in.
Tools for Black Box Testing
Below are some of the tools used for black box pen testing.
- QTP
- Selenium
- Loadrunner
- Jmeter
- Gremlin
- AutoHotkey
- IBM RFT
- Wireshark
- MbUnit
- Katalon
- OWASP ZEBEDIA
- Ranorex
- SilkTest
- Watir
Choosing the right pen testing tool depends on factors such as user interface, software integrations, usability, and pricing.
Black Box Penetration Testing Steps
Usually, black box penetration testing follows the following five steps.
- Reconnaissance: In this step, the tester gathers as much information as possible about the system being tested. This includes IP addresses, employee information, DNS records, and other public domain information.
- Scanning: In this step, the tester dives deeper into extracting additional information about the system. Details such as software, operating systems, connected systems, and user details are collected in this step.
- Discovering vulnerabilities: In this step, the tester uses different tools and techniques to look for vulnerabilities in the system. These techniques are decided depending on the information collected in the previous two steps.
- Exploitation: In this step, the tester exploits the vulnerabilities identified in the earlier step. The aim of this step is to get access to the system and cause the most damage in the least amount of time.
- Reporting and cleanup: In this step, the tester creates a report on the findings. Since the testing might have altered the state of the system, the tester also ensures that the system is returned to its original configurations.
Black Box Penetration Testing Cost
Black box pen testing is usually more expensive compared to white box testing. Since no prior information is provided about the system, it takes more time and effort to perform the penetration tests. The range of black box penetration testing can be anywhere from $4,000 to $50,000 per scan.
White Box Penetration Testing
As you might suspect, white box penetration testing—also known as clear box testing, glass box testing, transparent box testing, and structural testing—features a directly opposite approach to pen-testing. With this type of pen-testing, your tester will have full-disclosure, which includes their knowledge of IP addresses, source code, network protocols, and diagrams.
Additional features and benefits associated with white box testing include the following:
- Tests the Internal Structures of Your System vs. Functionality of Black Box Testing.
- Extends the Test Area.
When is White Box Testing Used?
White box pen testing is used in the scenarios described below.
- The system being tested is a critical system.
When testing critical systems, white box pen testing is recommended since it can perform thorough checks on the system’s defenses. With complete information of the system, the tester can evaluate the code paths, identify vulnerabilities, and perform checks on data encryption and protection.
- The system’s performance needs to be tested.
White box pen tests can help in testing the performance of the system by validating its internal algorithms.
- The system handles sensitive customer information.
When the system handles sensitive information, white box pen testing can be useful to test the database security and ensure that all security controls are working well.
- The goal is to perform thorough unit testing, integration testing, and code optimization.
This scenario is more from the point of view of software development. As part of the software testing, white box pen testing can be used effectively. It can also detect areas where the code can be optimized or improved.
Common White Box Penetration Testing Techniques
There are several white box penetration testing techniques. Some of the common testing techniques are the following.
- Statement coverage: Statement refers to the building blocks in the code that work together in the system. The statement coverage technique tests the functionality of each part of the code and checks whether all the statements are logically built.
- Data flow testing: This testing technique involves analyzing potential paths of data through the system. The test is performed to see how the data structures impact the program flow.
- Path testing: As the name suggests, this technique tests all paths or routes in the program. This ensures that all potential test scenarios and lines of code are tested.
- Control flow testing: This is a structural testing technique used to test the execution of statements and branches of source code. It helps determine the execution order of the instructions given.
Tools for White Box Testing
Below are some of the tools used for white box pen testing.
- JUnit
- Metasploit
- Wireshark
- NUnit
- John the Ripper
- Efix
- EclEmma
- Nmap
- Pytest
The white box pen testing tools are commonly used in other penetration tests, too.
White Box Penetration Testing Steps
Usually, white box penetration testing follows the below steps.
- Select the areas to be tested: For more efficient testing, it’s important to narrow down the core areas of the system that need to be tested. In this step, the tester also gathers and understands all the information about the programming language and tools used in development.
- Identify the code to be tested: In the next step, testers outline the lines of the code to be tested. How each part of the code works and the expected outputs are clearly defined.
- Write test cases: The test cases are written based on the vulnerabilities against which the system is being tested.
- Testing execution: Each scenario is tested to get to the root of each vulnerability in the system.
- Analyze results: The results of the tests are analyzed to plan how the vulnerabilities can be fixed. All analyses and plans for addressing vulnerabilities need to be recorded.
White Box Penetration Testing Cost
White box penetration testing is usually the cheapest pen testing method. The cost depends on the complexity of the system, the scope of the testing, the techniques being used, and the experience of the cybersecurity professional(s) performing the tests. The cost might sometimes also cover the remediation steps to be taken after identifying vulnerabilities. In this case, the cost would be higher.
Typically, white box testing can start at as low as $500 per scan. However, the total cost can go up to $7000+.
What is Gray Box Penetration Testing?
Gray box penetration testing is a hybrid method that combines the aspects of black box and white box pen testing. In this method, the tester has partial information about the system and its internal structure.
The gray box technique simulates the scenario where a potential hacker might have more information about the system through initial exploitation or inside information. Gray box testing provides a realistic analysis of the system since it operates from both insider and external perspectives.
Penetration Test Black Box vs. White Box
Here’s a comparison of black box pen testing vs white box pen testing.
| Criteria | Black Box Testing | White Box Testing |
| System information | Tester has limited knowledge about the system and no information about the internal structure, functionalities, and working. The focus is only on inputs and outputs. | Tester has complete information about the system including access to the source code, protocols, internal algorithms, etc. |
| Scope | Scope can be limited due to limited information at the time of testing. | Scope can be as wide as needed since the tester has all the information to conduct comprehensive testing. |
| Simulation style | Simulates an attack where the hacker has no information about the system. | Simulates an attack where an insider is involved, for example, a disgruntled employee with complete information about the system. |
| Advantages | Simulates real-world attack scenariosFaster methodCan identify system-level vulnerabilities | Can identify code-level vulnerabilitiesUseful for debugging during developmentThorough testing methodology |
| Disadvantages | Might miss some vulnerabilities due to limited informationCannot test all paths and scenariosLess suitable for software debugging | Might not be able to simulate actual attacker behaviorTime-consuming method |
| Use cases | Large scale and complex systemsIdentifying vulnerabilities that can be exploited from the outside | Debugging during software developmentIdentifying insider threats |
How to Choose the Right Pen Testing Provider?
Choosing the right pen testing provider is important so that their services are in line with your requirements and expectations. Below are a few useful tips to help you make the right choice.
- Identify your requirements. Assess your specific needs. Do you need to engage a pen testing provider for a one-time task or is it an ongoing requirement? What areas and systems do you need to focus on? These basic questions will help guide your selection.
- Check the provider’s experience and expertise. Checking the pen testing provider’s track record and ensuring that the team has good experience carrying out pen testing for other customers is a good way to vet them.
- Find out what testing methodology would be used. Since there are different pen testing methodologies and techniques, it helps to understand what the pen testing provider would suggest. For instance, AWA has several pen testing services like external pen testing, internal pen testing, mobile application pen testing, web application pen testing, etc.
- Check the pen testing provider’s pricing plans. Depending on your budget, cost can be an important consideration. AWA provides pen testing services at very competitive prices without compromising on the quality of their services through the CheckBox pen testing service.
- Check if the provider offers post-testing support. Some pen testing providers offer support after the testing is completed to help with remedial actions to address vulnerabilities. Depending on your in-house capabilities, this can be a useful consideration.
Perhaps you can easily determine what you need from the above descriptions. If not, AWA can help. Our team of penetration testers love digging into pen-tests and can help you figure out which type of test you need to serve your needs.
Request a free quote today.
FAQ
- What is a black box testing example?
Imagine a login interface for gaining access to an application. Black box testing for the login interface will not consider the source code. However, it will test how the login interface works when a username and a password are input.
The output could be a successful login on entering the right credentials, an error message on entering the wrong credentials, or a system crash when input values are invalid.
- What is an example of white box testing?
White box testing is used when the tester has complete information about the source code. An example of white box testing would be to perform tests on all types of inputs when there are multiple conditions in the code. For instance, if the system output is influenced by ‘n’ different input ranges, white box testing will include testing each condition by using at least one input from each range.
- Who uses white box testing?
White box testing is typically used during the software development process to perform unit testing, integration testing, and system testing. It is performed by professional penetration testers who have complete information about the source code, system protocols, and algorithms used in the system.
- Where is white box testing used?
White box testing is used for software debugging. It is also used to simulate insider threats and test the system response when someone from the inside tries to deliberately cause damage to the system.
- When should white box testing be used?
White box testing should be used for performing thorough software testing. It can be used to perform unit testing, integration testing, and system testing. It can also be used to identify system vulnerabilities by mimicking a potential insider attack by someone who has all the information about the system.
- What is black box vs gray box testing?
Black box testing is a penetration testing method where the tester has no information about the system. It simulates an external attack. On the other hand, gray box testing is a penetration testing method where the tester has limited information about the system. It simulates an attack where a potential hacker has access to insider information or has gained some level of access to the system via social engineering.
Have more questions about penetration testing? Read our detailed FAQs here.