Within today’s world, compliance is a top priority of the masses. Compliance with various security regulations and frameworks not only helps to ensure a company’s overall security, but it is also a valuable marketing strategy that is used to promote a company’s commitment to security.
What is PCI DSS and why do some companies need to be PCI DSS compliant?
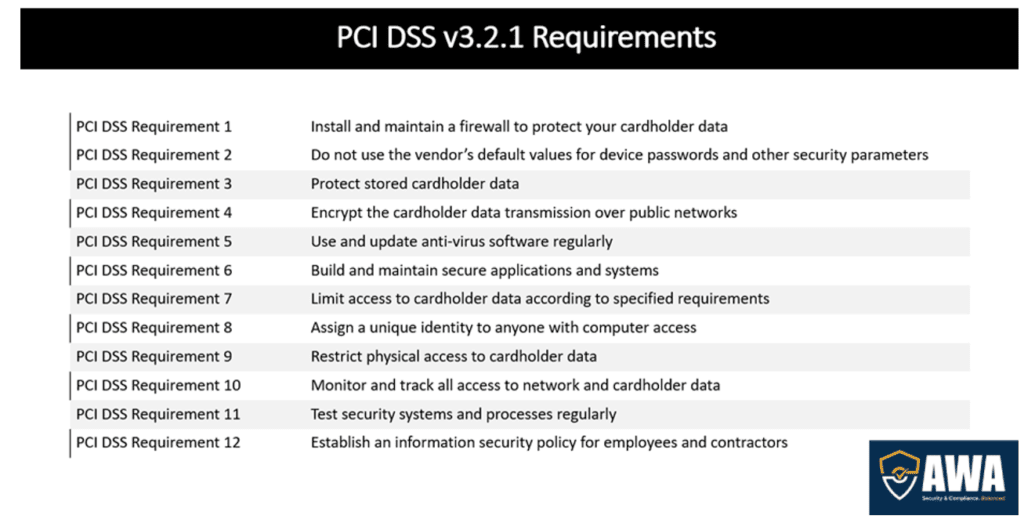
The Payment Card Industry Data Security Standard (PCI DSS) is mandated by major credit card brands but administered by the Payment Card Industry Security Standards Council. The standard was created to increase security controls around cardholder data to reduce credit card fraud. PCI DSS is mandatory for any organization that accepts, transmits, or stores cardholder data, however many organizations that may or may not handle cardholder data still strive for PCI DSS compliance. While most companies are compliant with PCI DSS version 3.2.1, a new version (4.0) was recently released and will eventually replace the old version.
Requirement 12.2 – Cybersecurity Risk Assessment
Within high-level Requirement 12 of the PCI DSS, organizations are responsible for performing annual cybersecurity risk assessments across the organization, particularly within their cardholder data environment (CDE). This is to ensure potential risks related to data transmission and storage are identified, measured, and managed to assist in providing consumers with assurance that their data is secure.
Below are the 5 steps to complete a PCI Cybersecurity Risk Assessment:
- Map Card Data Flow
- Where does cardholder data enter the organization?
- Where does the system process cardholder data?
- Where does cardholder data leave the organization?
- Where does the system store cardholder data?
- Identify Vulnerabilities, Threats, and Risks
- Organizational flaws
- Technical flaws
- Environmental flaws
- Analyze Risk Level
- Risk rating
- Risk likelihood
- Risk impact
- Create a Risk Management Plan
- Identify security controls implemented and method of maintaining
- Prioritize highest risk areas
- Create PCI Documentation
- Cybersecurity Risk assessment report
Cybersecurity Risk Assessment Precursors
There are some common security practices that should be performed by all organizations prior to conducting a cybersecurity risk assessment:
- Internal & External Vulnerability Scans. Vulnerability scans are a recognized way to identify possible holes within a network where malicious actors can enter.
- Penetration Tests. While vulnerability scans identify possible holes, penetration tests utilize these results and attempt to exploit possible vulnerabilities. This practice takes vulnerability management to the next level to ensure any exploitable vulnerabilities are promptly remediated.
Evaluating Your Cybersecurity Risk Management Program
Not sure where to begin? Let AWA International Group help by performing a PCI DSS Gap Analysis. During a PCI DSS Gap Analysis, AWA will help achieve the following:
- Advice on the organization’s current cybersecurity risk assessment strategy
- Identify existing security controls & gauge strengths / weaknesses
- Conduct vulnerability scans
- Perform penetration tests
- Analyze gaps in current capabilities
- Measure security maturity against the PCI DSS







