Congratulations – you’ve officially migrated to one of the industry-leading cloud providers and the hard work is done! However, now is not the time to bow your head when it comes to data security. To ensure your organization benefits from what cloud hosting has to offer, it’s important that CSPM is also in place. But what is CSPM?
Cloud Security Posture Management (CSPM) is defined as “a continuous process of cloud security improvement and adaptation to reduce the likelihood of a successful attack.”
In this blog, we highlight some of the Top Cloud Providers, Top Cloud Security Threats, and Top Cloud Security Best Practices to guide you on the right track.
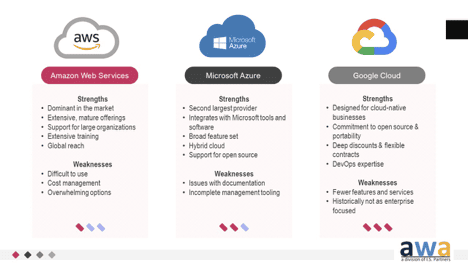
Cloud Hosting – Key Players
Top 5 Cloud Security Threats
There are numerous reasons why businesses today are moving to the cloud. Some of these include efficiency, accessibility, fast speeds… the list goes on. It is also thought that the cloud is “safe” from hackers. The truth is that while it is a secure option, the cloud also introduces a new/different set of security risks. Hackers have realized that businesses are using the cloud more than ever, so they have adjusted their approach for today’s world. Many times, hackers take advantage of an organization’s lack of knowledge around cloud security controls.
Below are the top 5 cloud security threats that organizations should still be cautious of –
- Data Breaches:
- Lack of data value definition & loss impact
- Failure to regularly review access to critical or sensitive data
- Misconfiguration
- Inadequate encryption methods
- Inadequate incident response plan
- Insufficient identity, credential, access & key management:
- Failure to use strong passwords
- Failure to use multi-factor authentication
- Inadequately protected credentials
- Lack of automated rotation of cryptographic keys, passwords, and certificates
- Insecure interfaces & APIs:
- Inadequate protection of API keys
- Reusage of API keys
- Inadequate penetration testing
- Account hijacking:
- Failure to address the root cause of stolen account credentials
- Weak Identity Access Management (IAM) controls
- Insider threats (intentional or negligent):
- Poor security education & training for employees/contractors
- Failure to regularly audit server configurations
Top 5 Cloud Security Best Practices
As you can see, choosing a cloud hosting provider does not mean your organization is off the hook for ensuring data security. While hosting providers typically offer several monitoring and alerting services to help prevent a potential security incident, there are still things your organization is responsible for to strengthen your security posture.
To keep your organization’s data safe and secure, it is of the utmost importance that your cloud environment is configured based on your hosting provider’s best practices. In addition to this, below are the general top 5 cloud security best practices that the organization should consider –
- Carefully choose your cloud vendor
- Evaluate security capabilities and levels of compliance
- Ensure 24/7 data and network availability
- Define vendor and organization responsibilities
- Implement endpoint security
- Ensure password protection
- Enable multi-factor authentication
- Install and manage endpoint antivirus/anti-malware
- Securely manage data
- Identify data value & loss impact
- Implement appropriate encryption protocols
- Ensure least privilege / role-based access in place
- Monitor & prevent
- Understand limits of cloud provider
- Implement IDS/IPS
- Configure monitoring alerts
- Conduct due diligence
- Regularly review logical & physical access controls
- Annual incident response testing
- Annual Penetration testing
- Quarterly Vulnerability scanning
- Routine third-party assessments
Evaluating Your Cloud Security Posture – Where to begin?
After you’ve implemented your cloud hosting provider’s recommended security practices and general cloud security standards, your organization should still plan to regularly evaluate the cloud infrastructure as it relates to your business’s use case. If you aren’t sure where to start, let AWA International Group help by performing a Cloud Environment Security Assessment. During a Cloud Environment Security Assessment, AWA will help achieve the following:
- Identify cloud security risks
- Identify existing security controls & gauge strengths / vulnerabilities
- Analyze gaps in current capabilities & advise solutions
- Measure security maturity against industry standards
- Assess effectiveness of current cloud security policies
- Generate reports on compliance with the CIS Framework, AWS Well Architected Framework, and Microsoft Azure Best Practices