According to Mordor Intelligence, the increase in the number of cyber attacks and compliance requirements are pushing more and more organizations to include penetration testing in their cybersecurity strategy. The increasing number of wireless networks, growing internet activity, and rapid cloud adoption are also driving factors for the interest in penetration testing.
In this article, we will go over why penetration testing is important and how organizations can leverage different types of penetration testing methods to strengthen their cybersecurity posture.
What is penetration testing?
The basics first. Penetration testing is a planned, simulated attack against your systems and network to identify vulnerabilities that can be exploited by hackers. Penetration testing is carried out by professional ethical hackers (or pen testers) who will try to mimic a real-life cyber attack to test the defenses.
Penetration testing is a security exercise that helps to find the chinks in the cybersecurity armor so that fixes can be applied proactively. The ultimate goal is to ensure that the organization’s security infrastructure is robust enough.
Why is penetration testing important?
Penetration testing is important because it helps you identify system and network vulnerabilities before a hacker does. Think of pen testing as a fresh perspective to look for known and unknown vulnerabilities. It is a testing approach that is part of the holistic cybersecurity strategy.
Below is a summary of the reasons why pen testing is important for organizations.
- Identifying vulnerabilities: Pen testing helps to identify vulnerabilities in systems, networks, mobile and web applications, etc. These vulnerabilities, when left unattended, can be exploited by cyber criminals.
- Risk identification and assessment: Penetration testing can be an important step for an organization’s risk management strategy. It can reveal the level of risk exposure so that you can prioritize risk management activities.
- Preventing data breaches: Pen testing can help identify vulnerabilities that can cause data breaches. When you proactively address these vulnerabilities, it improves the information security posture.
- Compliance requirement: Certain regulatory frameworks require that organizations perform penetration tests. This not only helps maintain a good security posture but also ensures that the organization avoids legal or regulatory non-compliance.
- Third-party risk management: Several organizations often work with third-party entities. This might inadvertently expose them to a variety of threats. Pen testing can expose these threats so that they are addressed accordingly.
- Enhanced reputation: An organization that includes penetration testing in its cybersecurity strategy demonstrates its commitment to enhanced information security, thus building credibility and trust with all stakeholders.
- Security training: Since penetration testing simulates a real attack, it is a good opportunity to train the security staff on how to respond to a security incident.
When do you need to conduct penetration testing?
Penetration testing is an important tool for cyber security. However, the entire process can often be time-consuming and expensive. Hence, it is necessary to identify when an organization needs penetration testing.
There are several situations when penetration testing would be recommended. Below is a summary of different scenarios.
Penetration testing before a new launch
Conducting penetration testing before a new launch helps you identify vulnerabilities before the system is exposed to the live environment and potential hackers. Hence, it is recommended that you conduct pen tests before deploying a new system, application, network, or any other IT infrastructure.
Penetration testing after a major change
Any major changes such as upgrades, migrations, the addition of new systems, etc. warrant penetration testing. This helps identify any new vulnerabilities that the new changes might have introduced.
Penetration testing for regulatory compliance
Certain regulatory frameworks and standards require that penetration testing is carried out. For example, PCI DSS, SOC 2, HIPAA, etc. require penetration testing. If your organization needs to comply with these standards, you will need to schedule penetration tests.
Penetration testing after a data breach
If your company has been subjected to a data breach, a pen test should be a part of your company’s remediation strategy to identify additional system vulnerabilities and fix them immediately. It is a good strategy to enhance your security strategy and prevent any future data breaches. It’s also a good tool to demonstrate concrete action and rebuild trust in your organization.
Penetration testing after M&As and new vendor onboardings
When your organization is part of mergers or acquisitions or starts an engagement with new vendors, it is exposed to new systems, networks, and integrations. Pen testing can help evaluate the overall security in such cases.
Penetration testing for certain industries
Certain industries such as healthcare or financial institutions have a lot at stake in case they face a security breach. If your organization deals with sensitive data or faces severe financial consequences as a result of a breach, penetration testing should be prioritized for proactively addressing risks.
Penetration testing as a first-time exercise
If for any reason your organization hasn’t yet undergone penetration testing, now is as good a time as any. Small businesses might often make the mistake of assuming that they are of no interest to hackers. However, small businesses account for 46% of all attacks. It’s always a good idea to schedule your first penetration test at the earliest and take your cybersecurity journey further.
What are the main types of penetration testing methods?
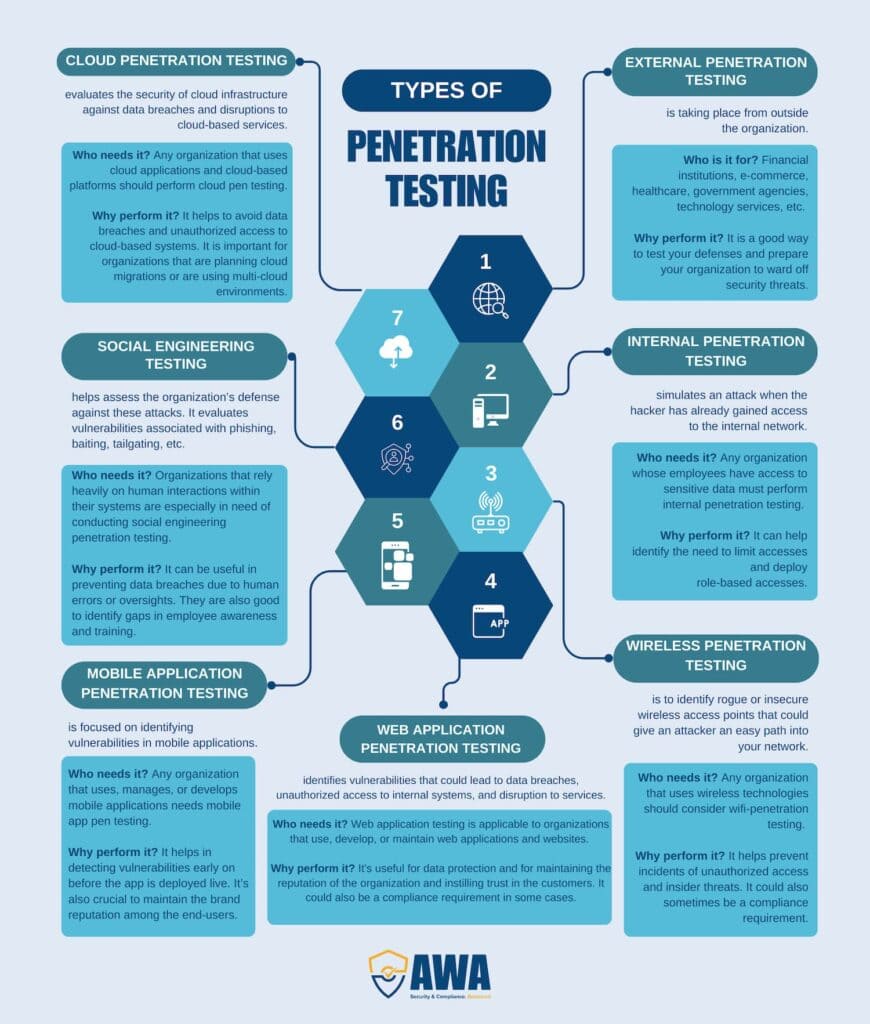
There are several different types of penetration testing methods to suit your business and security goals, industry type, organization complexity, etc. The 7 main penetration testing methods are mentioned below.
- External penetration testing
External penetration testing is a method of testing taking place from outside the organization. It simulates an outside attack with no information about the system, its weaknesses, the code involved, etc.
Who is it for? External penetration testing is applicable to a wide range of industries and organizations of all sizes. Financial institutions, e-commerce, healthcare, government agencies, technology services, etc. are a few examples where external penetration testing is applicable.
Why perform it? External penetration testing simulates a real-life attack by malicious actors. It is a good way to test your defenses and prepare your organization to ward off security threats.
- Internal penetration testing
Internal penetration testing simulates an attack when the hacker has already gained access to the internal network. This attack could simulate a successful phishing attempt or a disgruntled employee trying to cause damage to the systems or network.
Who is it for? Any organization whose employees have access to sensitive data must perform internal penetration testing. Healthcare, finance, education, retail, manufacturing, etc. are the types of industries that can benefit from internal penetration testing.
Why perform it? Internal penetration testing reveals the extent of damage a malicious actor can cause when they have access to internal information. It can help identify the need to limit accesses and deploy role-based accesses.
- Wireless network penetration testing
Wireless penetration testing is also known as wifi penetration testing. The focus of this type of penetration testing is on identifying vulnerabilities in wireless networks and related components and infrastructure.
The goal is to identify rogue or insecure wireless access points that could give an attacker an easy path into your network.
Who needs it? Any organization that uses wireless technologies should consider wifi-penetration testing. Since most organizations will use wifi for communication, data transfer, and connectivity, the testing is applicable to a wide array of industries and organizations of different sizes. Situations where public wifi network is provided such as airports and malls also need wifi pen testing.
Why perform it? Wifi pen testing helps prevent incidents of unauthorized access and insider threats. It could also sometimes be a compliance requirement.
- Web application penetration testing
Web application penetration testing focuses on identifying vulnerabilities in web applications, websites, online platforms, and APIs. It identifies vulnerabilities that could lead to data breaches, unauthorized access to internal systems, and disruption to services.
Who needs it? Web application testing is applicable to organizations that use, develop, or maintain web applications and websites. This makes it an important consideration for almost all organizations that might have an online presence.
Why perform it? This type of penetration testing is useful for data protection and for maintaining the reputation of the organization and instilling trust in the customers. It could also be a compliance requirement in some cases.
- Mobile application penetration testing
Mobile application penetration testing is focused on identifying vulnerabilities in mobile applications. Given the rise in the use of mobile apps, this type of testing ensures that safe and secure apps are deployed.
Who needs it? Any organization that uses, manages, or develops mobile applications needs mobile app pen testing. App developers might also need the testing to get their app approved on app stores.
Why perform it? Mobile app pen testing helps in detecting vulnerabilities early on before the app is deployed live. This helps in preventing security breaches. It’s also crucial to maintain the brand reputation among the end-users.
- Social engineering penetration testing
Social engineering is one of the growing causes of data breaches and social engineering testing helps assess the organization’s defense against these attacks. It evaluates vulnerabilities associated with phishing, baiting, tailgating, etc.
Who needs it? Organizations that rely heavily on human interactions within their systems are especially in need of conducting social engineering penetration testing.
Why perform it? Social engineering tests can be useful in preventing data breaches due to human errors or oversights. They are also good to identify gaps in employee awareness and training.
- Cloud penetration testing
Cloud penetration testing is gaining importance with the increased adoption of cloud services across various industries. It evaluates the security of cloud infrastructure against data breaches and disruptions to cloud-based services.
Who needs it? Any organization that uses cloud applications and cloud-based platforms should perform cloud pen testing. Since cloud adoption has been growing in several industries, it is becoming an important testing method for companies of all sizes.
Why perform it? Cloud penetration testing helps to avoid data breaches and unauthorized access to cloud-based systems. It is important for organizations that are planning cloud migrations or are using multi-cloud environments.
How to choose the right penetration testing company?
Now that we have covered the different types of penetration tests and covered in detail why you need to perform the testing, it’s time to choose the right company for performing the penetration testing.
When you choose the right vendor for pen testing, you are taking a step toward ensuring better security for your organization’s systems, networks, and information. Below are the best practices to help you make the right choice.
- Define the scope of your requirement. This includes identifying your goals for penetration testing and defining what type of pen testing you might need. The scope should define the systems, networks, software products, devices, etc. that need to be tested.
- Evaluate the skills of the company and review their certifications. You need a company that has pen testers with a demonstrated experience in pen testing. One way to check this is also to look at the certifications. Some of the relevant certifications include:
– Offensive Security Certified Professional (OSCP)
– Certified Ethical Hacker (CEH)
– Certified Information Systems Security Professional (CISSP)
– GIAC’s Penetration Testing Certification (GPEN)
– Licensed Penetration Tester (LPT)
There could be other certifications that are relevant to the type of testing you are looking for.
- Check for the track record. Request information about the company’s experience in conducting penetration testing. Case studies and reviews from previous clients can be helpful. You can also ask for references to check the track record.
- Ask about the methodologies and techniques the company will employ. The methodologies and techniques used in penetration testing should align with your scope and objectives.
- Request a sample report. A sample report will give you an idea about the company’s reporting style and also insights into how thorough the penetration testing would be. It will also help you understand what to expect in terms of analysis and recommendations.
- Check how your data would be handled. Pen testing will expose critical information to the company performing these tests. Thus, do check how the company handles and protects your data.
- Clarify the engagement model. In most cases, pen testing would be a regular activity. Hence, it helps to check what engagement model the company offers. Ongoing support, post-testing assistance for fixing vulnerabilities, and regular pen testing services should be considered.
- Compare pricing. Consider the pricing structure offered and compare it with other vendors. The pricing should be in line with the quality of the services provided and your organization’s budget considerations. AWA provides extremely competitive pricing without compromising on quality under their CheckBox Penetration Testing service.
AWA has a team of experts in the different types of penetration testing methods. By employing the latest tools and technologies, AWA ensures that you always get comprehensive penetration testing solutions that are customized for your specific requirements.
Still wondering whether penetration testing is the right choice for you? These 6 questions about penetration testing will bring some clarity!
Frequently Asked Questions
- What are the three approaches to pen testing?
The three approaches to penetration testing are Black Box Penetration Testing, White Box Penetration Testing, and Grey Box Penetration Testing.
- What are the 6 main types of penetration testing?
There are various types of penetration testing. The 6 main types of penetration testing are:
- Internal penetration testing
- External penetration testing
- Wi-Fi penetration testing
- Web application penetration testing
- Mobile application penetration testing
- Social engineering penetration testing
- How often should penetration testing be performed?
Penetration testing should be performed regularly and at least once every year.
The frequency of penetration testing depends on several factors. These include:
- Risk profile
- Compliance requirements
- Industry regulations
- Changes in the IT infrastructure
Critical systems need more frequent pen testing compared to low-risk systems.
- What is the difference between pen testing and vulnerability scanning?
Vulnerability scanning is a high-level activity. It usually employs automated tools to look for vulnerabilities in the systems or networks being scanned. On the other hand, pen testing is a planned simulation that looks at vulnerabilities in detail. Pen testing is carried out by professionals.
Learn more about the key differences between vulnerability scans and pen tests here.
Vulnerability assessments and penetration tests work together to fortify your cybersecurity.